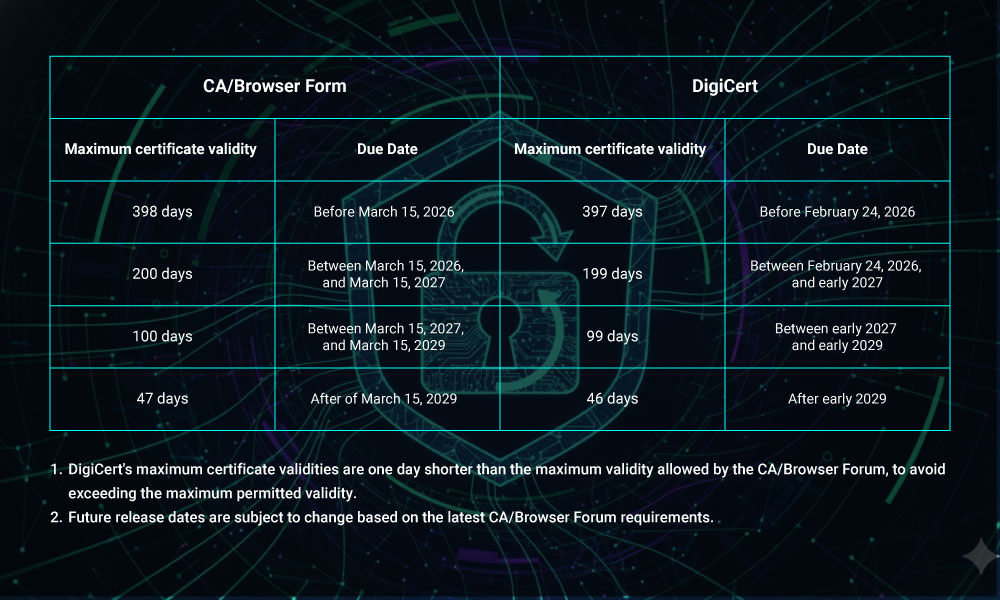
DigiCert has officially announced an update to public TLS/SSL certificate issuance rules, confirming that the maximum validity period for public TLS certificates will be reduced to 199 days, effective 24 February 2026. This update applies to all public TLS certificates, including DV, OV, and EV. While the change introduces operational considerations, it also highlights the growing importance of structured certificate management.
Why is DigiCert reducing the maximum validity of public TLS certificates to 199 days?
DigiCert is making this change to align with the CA/Browser Forum’s Ballot SC081v3: Introduce Schedule of Reducing Validity and Data Reuse Periods. This ballot sets a timeline for all Certificate Authorities (CAs) to reduce TLS certificate validity from 398 days to 200 days in 2026, 100 days in 2027, and 47 days in 2029. Learn more about Ballot SC081v3.
What Is Changing?
Historically, public TLS certificates could be issued for up to 397 days. Under the new rules:
- From 24 February 2026, the maximum validity for newly issued public TLS certificates will be 199 days
- Certificate requests exceeding this validity will no longer be accepted
- Certificates issued before this date will remain valid until their expiry
- The change applies across all public TLS certificate types
Further reductions in certificate validity are expected in the coming years as part of long-term industry security initiatives.

Why the Industry Is Moving to Shorter Validity Periods
Shorter certificate lifetimes are intended to:
- Reduce exposure in the event of key compromise
- Encourage faster adoption of updated security standards
- Support automation and improved certificate hygiene
This shift reflects a broader trend toward continuous security management rather than long-duration trust models.
Implications for Resellers
For resellers managing SSL certificates across multiple customers or domains, shorter validity periods introduce several practical considerations.
1. More Frequent Certificate Activity
Certificates will need to be renewed or reissued more often, increasing the importance of visibility and tracking across portfolios.
2. Higher Operational Dependency
Customers may rely more heavily on resellers for:
- Renewal reminders
- Deployment coordination
- Avoiding service disruption caused by expired certificates
3. Greater Emphasis on Process
Manual renewal workflows that worked previously may become less sustainable, particularly at scale.

The Role of Automation and Planning
As certificate lifecycles shorten, automation becomes increasingly relevant. Approaches such as:
- ACME-based renewals
- Centralised Certificate Lifecycle Management tools
can help reduce administrative effort and minimise the risk of missed renewals.
Early planning including reviewing existing processes and educating customers will be key to adapting smoothly to the new requirements.

How WebNIC Supports Resellers
WebNIC works with resellers to help them adapt to evolving industry requirements by providing:
- Access to trusted DigiCert TLS/SSL certificates
- A reseller platform designed to manage certificates efficiently
- Guidance on industry changes and best practices
- Support for resellers serving both SMB and enterprise customers
Our focus is on enabling resellers to manage certificate changes with clarity and confidence.
Preparing Ahead of 2026
Resellers may consider taking the following steps:
- Review current SSL certificate portfolios and renewal cycles
- Inform customers about upcoming validity changes
- Assess whether existing workflows can support shorter lifecycles
- Plan certificate orders and transitions ahead of the February 2026 deadline
Taking a structured, informed approach helps minimise disruption and ensures continued trust.
Conclusion
The move to 199-day public TLS certificate validity represents an important evolution in web security standards. For resellers, the change underscores the need for clear processes, effective communication, and thoughtful planning.
WebNIC remains committed to supporting resellers as certificate management practices continue to evolve.

